Privileged Access Management
The BeyondTrust Privileged Access Management portfolio is an integrated solution that provides visibility and control over all privileged accounts and users. By uniting the broadest set of privileged security capabilities, the platform simplifies deployments, reduces costs, improves usability, and reduces privilege risks.
80% of Breaches are the Result of Privileged Credential Abuse or Misuse
Videos
-

BeyondTrust Solutions Overview
-

Technology Alliance Partners
-

Understanding Ransomware and What You're Up Against
-

BeyondTrust Privileged Remote Access
-

How is BeyondTrust making a difference in cybersecurity?
-

BeyondTrust Remote Support
-

BeyondTrust: Journey to Achieving Universal Privilege Management
-

BeyondTrust: What Is Universal Privilege Management (UPM)?
Privileged Access & Session Management
BeyondTrust offers the broadest set of credential management capabilities in solutions tailored to address your specific risks and use cases.
Whether your IT infrastructure is entirely in the cloud or is a hybrid model, BeyondTrust solutions will work for your needs.
Password Safe
Reduce the risk of privileged credential misuse through automated password and session management. Secure, control, monitor, alert and record access to privileged accounts.
Continuously discover and onboard accounts. Leverage powerful threat analytics and reporting to address compliance requirements.

Continuous Auto-Discovery
Scan, identify and profile all assets and applications with auto-onboarding of privileged accounts
Discover and profile all known and unknown assets (web, mobile, cloud, virtual), privileged user accounts, shared accounts, and service accounts
Automatically bring systems and accounts under management
Create Smart Groups to automatically categorize, group, assess, and report on assets by IP range, naming convention, OS, domain, applications, business function, Active Directory, and more.
Privileged Session Management
Store, manage and rotate privileged account passwords, eliminating embedded credentials and ensuring password strength.
Request RDP/SSH access to authorized systems only
Start sessions instantly, or via workflow
View any active privileged session, and if required, pause or terminate the session
Use keystroke indexing and full text search to pinpoint data, and then log an acknowledgement of the review for audit purposes
Avoid Java – Password Safe is a client-less solution with no agents required on the server
Fully integrate with native tools (MSTSC, PuTTY, MobaXterm etc.)
Gain full video recording with 100% accountability

Securing Application Credentials
Control scripts, files, code and embedded keys to close back doors to your critical systems
Enables removal of hard-coded passwords from applications and scripts
Provides an extensible REST interface that supports many languages, including C/C++, Perl .NET, and Java
Ensures that passwords can be automatically reset upon release
Enforces extensive security controls to lock down access to only authorized applications
Cloud Vault
Cloud Vault provides fast, essential vaulting capabilities for privileged accounts, from local or domain shared administrator, to a user’s personal admin account, even SSH keys.
BeyondTrust Privileged Remote Access, it gives you a Privileged Access Management powerhouse, enabling your organization to manage both privileged sessions and passwords as well as vendor access in one solution.
Discover and Vault Passwords
Discover, manage, and rotate privileged credentials for Windows platforms and seamlessly inject those credentials on-demand, whenever they are needed.
Fully manage Windows local and Active directory privileged accounts via discovery and automatic rotation.
Safely store, retrieve and inject any username/password or SSH key combination that is associated with specific user or shared admin account all with robust auditing and monitoring for every privileged account utilized.
Increase security and reduce the risk of a cyber-attacks by consolidating the tracking, approval, and auditing of privileged accounts in one place and by creating a single access pathway.
Enhanced Session Management
Control access to and from any system you manage, no matter the
platform or environment, and eliminate inefficient manual workflows.
End to end security for remote access sessions, from any location via any device, to any endpoint without revealing privileged passwords.
Improve productivity by allowing administrator accounts to access systems with just the click of a button, no more wasted time finding or tracking down credentials.

Meet Compliance Requirements
Create a comprehensive, automated audit trail of all user activity, complete with video recordings, logs, and session forensics.
Create audit trails and enable session forensics by capturing detailed session data in real-time or for post- session review.
Easily create attestation reports to prove compliance.
DevOps Secrets Safe
Credentials and secrets used in DevOps environments are a prime target for attackers. Using a DevOps tools-centered approach to manage secrets contributes to secrets sprawl and expands the attack surface. Implementing a centralized administration solution, built for continuous development environments with security as the driving factor reduces the risk of exposure without slowing down the application delivery process.

Implement Secrets Management Best Practices
Secure and automate the storage and access of secrets used by applications, tools, and other processes across your development operations environments.
- Bring all secrets and privileged credentials used by applications, tools and other non-human identities under centralized administration.
- Mitigate the risk of downtime.
- Create an audit trail of all secrets operations so you always know who accesses what and when.
- ability to audit the entire secrets life cycle.

Integrate with DevOps Tools
Enable faster application delivery via frictionless native integrations with common DevOps tools such as Ansible, Jenkins, and Azure DevOps.
- out-of-the-box integrations to secure and manage secrets used by applications and common DevOps tools.
- Integration with common identity repositories for authentication.
- REST APIs to facilitate development workflows and a Command Line Interface (CLI) tool allows for easy API interaction, enabling velocity and agility for DevOps teams.
BeyondTrust Ecosystem
Endpoint Privilege Management
Stop malicious attacks, including malware and ransomware, by assigning just-in-time privileges and controlling applications on Windows, Mac, Unix, Linux, and networked devices – all without hindering end-user productivity.
Bridge the gap between Windows and other operating systems by extending Active Directory’s Kerberos authentication and single sign-on (SSO).
Privilege Management for Windows and Mac
BeyondTrust Privilege Management for Windows and Mac is designed to deliver a fast time-to-value and minimize business disruption. Unlike traditional privilege management products that can take months to properly configure, we get you up and running in mere hours. We’ve leveraged years of deployment scenarios to create out-of-the-box workstyles meant to cover the vast majority of enterprises and significantly reduce implementation efforts.
Elevate Applications, Not Users
Maintain security, user productivity, and IT operational efficiency by enforcing least privilege across the desktop environment
- Secure your organization from attacks against trusted applications, that remain a threat even if you’ve removed admin rights.
- The pre-built templates within Trusted Applications Protection stop attacks involving trusted apps, catching bad scripts and infected email attachments immediately.
- Use it to protect trusted applications such as Word, PowerPoint, Excel, Adobe Reader, common web browsers, and more by controlling their child processes and DLLs.

Track and Control Applications
Protect endpoints from infection by whitelisting approved applications and checking for vulnerability status
- Deliver trust-based application whitelisting with a flexible policy engine.
- Automated whitelists including applications that are allowed through Group Policy.
- Block or allow applications for each group of users
- Improve compliance by tracking processes, installations, and attempted installations
- Add applications to policies with simple copy & paste
- Whitelist applications based on publisher, hash, or other flexible methods

Analyze User Behavior
Analyze user behavior by collecting, storing and indexing keystroke logs, session recordings and other privileged events
- Provide a single audit trail of all user activity to streamline forensics and simplify compliance.
- Refine and improve you security policies.
- Privileged account protection logs
- Trusted Application Protection events
- Powerful Custom reporting
Privilege Management for Unix, Linux, and Networked Devices
Unix and Linux systems present high-value targets for external attackers and malicious insiders. The same holds true for networked devices, such as IoT, ICS and SCADA. Gaining root or other privileged credentials makes it easy for attackers to fly under the radar and access sensitive systems and data. BeyondTrust Privilege Management for Unix & Linux is an enterprise-class, gold-standard privilege management solution that helps security and IT organizations achieve compliance, control privileged access, and prevent and contain breaches that can affect Unix and Linux systems – without hurting productivity.

Control Root Privileged Access
Utilize factors such as time, day, location and application/asset vulnerability status to make privilege elevation decisions.
- drive password updates with a single functional account on a single server.
- elevate privileges for standard users on Unix and Linux through fine-grained, policy-based controls.
- Provide fine-grained privilege elevation rules to perform only specific tasks or commands.
- Enable users to run specific commands and conduct sessions remotely based on rules without logging on as admin or root.
- Regardless of how a session is established to your Unix/Linux host, fine-grained control over what the user can do once they are connected to a target machine.

Audit User Activity
Audit and report on changes to critical policy, system, application and data files.
- Analyze user behavior by collecting, securely storing and indexing keystroke logs, session recordings and other privileged events.
- Protect against unauthorized changes to files, scripts and directories.
- The system allows for policies around the Who, What, Where, and When of every command, with deeper auditing beyond that of simple session recording.
- Granular control of proxied sessions and direct sessions covers all your system access needs, not just those that fall into break-glass situations.
Monitor and Replay
Detect suspicious user, accounts, and asset activity in real time or on replay.
- Elevated commands are recorded in the event log, so we know which commands were attempted and whether or not they ran elevated.
- Session recording begins on the policy server before the command is elevated.
- SSH sessions can be recorded directly on one or more log servers, simplifying functions such as log review and log archiving.
Active Directory Bridge
BeyondTrust AD Bridge centralizes authentication for Unix, Linux and Mac environments by extending Active Directory’s Kerberos authentication and single sign-on capabilities to these platforms. By extending Group Policy to non-Windows platforms, BeyondTrust provides centralized configuration management, reducing the risk and complexity of managing a heterogeneous environment.
- Allow users to leverage their AD credentials to access Unix, Linux or Mac systems
- Working consistently by extending native group policy management tools to include settings for Unix, Linux and Mac
- Audit several events in real time by accessing results through the BeyondTrust console or forward to third-party solutions
- Transition users from desktops to remote machines or between systems, without requiring them to re-enter credentials
- Consolidate directories to simplify management of complex environments
Provide a single familiar toolset to manage both Windows and Unix systems. Perform account maintenance and password updates through a single directory administration tool (Active Directory Users and Computers).
- Enables one-to-many management of Unix, Linux, and Mac OSX configuration settings.
- Leverage existing Active Directory deployments to centrally manage heterogeneous workstations and users.
- Provides a pluggable framework with an interface similar to Microsoft’s Management Console on Linux or Mac OS X.
- Allow users to use their Active Directory credentials (Username and Password) to gain access to Unix, Linux and Mac, removing the need to manage user accounts separately on Mac workstations and server platforms.
- Full support for Apple’s Workgroup Manager application, allowing for seamless management and control of Mac system settings.
Provide audit details to audit and compliance teams and manage group policies centrally. BeyondTrust AD Bridge is the only solution that does not have to modify your Active Directory schema to add Linux, Unix, & Mac OS X systems to your network.
- Effortlessly manage and view access privileges for users and groups through customizable reports.
- Provide audit details to audit and compliance teams via enterprise-spanning access and authorization reports.
- Extend the capabilities of native group policy management tools to include specific group policy settings for Unix, Linux and Mac – achieving a consistent configuration across the enterprise.
- Amazing flexibility for compliance according to ISO27001 that requires centralized credentials’ management for all systems.
Expand single sign-on (SSO) and file sharing, and control access to non-Windows systems for enhanced security across all systems in the organization.
- Get single sign-on for any enterprise application that supports Kerberos or LDAP, including Samba, Apache, SSH, Websphere, JBoss, Tomcat, Oracle, and MySQL.
- Support for Remote Network file share access for Mac and Linux systems.
- Centrally control access to non-Windows systems by defining which users are permitted to log onto which systems via Active Directory.
Secure Remote Access
Privileged Remote Access allows you to secure, manage, and audit vendor and internal remote privileged access without a VPN.
With Remote Support, you can empower the service desk to support Windows, Mac, Linux, iOS, Android, network devices, and peripherals with one, secure tool.
Privileged Remote Access
Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault. Or you can integrate it with BeyondTrust Password Safe or another Password Management Solution.
This password component enables our credential injection capabilities. Instead of requiring privileged users to know usernames and passwords for each endpoint, we can store those credentials securely. And then, using API functionality, we can retrieve those credentials and inject them directly into a session.

Privileged Access Control
Enforce a policy of least privilege by giving users just the right level of access needed for their roles with individual accountability for shared accounts.
- Define what endpoints users can access, schedule when they can access them, and whitelist / blacklist applications for a comprehensive approach to privileged access.
- Control and monitor sessions via a secure agent or using standard protocols for RDP, VNC, Web, and SSH connections.
- Set authorization and notification preferences to be alerted when a user is accessing Privileged Remote Access.
- Administrators can use their mobile devices to approve requests and monitor access usage from anywhere.

Work Across Hybrid Environments
Simplify the access process by providing one tool that facilitates all unattended access for remote systems and endpoints
- In addition to desktop consoles for Windows, Mac, and Linux, BeyondTrust Privileged Remote Access includes mobile apps and a browser console.
- By automating processes with features like credential injection and integrations with SIEM and change management solutions, your technicians can increase productivity and security at the same time.
Cloud & Virtualization Security
Effectively manage privileged access to business assets that leverage web-based management consoles, including IaaS servers, hypervisor environments, and web-based configuration interfaces for core network infrastructure.
- Leverage Existing Security Investments, by increasing the security of IaaS accounts with individual accountability for root accounts
- Advanced Web Access supports can be configured to work with all Public Cloud Providers including Amazon Web Services, Google Cloud, Microsoft Azure, IBM Cloud, Rackspace and others
- Advanced Web Access works with virtualization systems including VMware vSphere, Citrix XenServer, Microsoft Hyper-V, KVM and others
Secure Remote Support
Support all of your systems over the web, even if they are behind firewalls you don’t control. All supported platforms are included in the core product, so you can consolidate and standardize support, improving incident handling time and support rep productivity.
BeyondTrust Remote Support works across Windows, Mac, Linux, Android, iOS, and Chrome OS. Access and control any remote computer or device, on or off the network – no VPN required.

Remote Access & Control
Provide fast remote assistance to any desktop, server, or mobile device, with screen sharing and remote control – anytime, from anywhere
- Provide instant, reliable remote support to end-users and customers on or off your network.
- Be more productive, focusing on fixing issues, not fixing the connection.
- Granularly manage team users, roles, and session permission settings to enforce a least privileged security posture
- Integrate with CRM, ITSM, SIEM, and password tools or use BeyondTrust’s open API and to create custom integrations

Audit & Compliance
Log all session activity for a complete audit trail, with real time reporting and capture a detailed video log of all session activity
- Improve service levels and customer satisfaction with seamless, high-quality remote support for every end-user.
- Provide scalable, enterprise-grade support that keeps your business running, whether you’re fixing a Linux server across the ocean or an iPhone across town.
- Maintain corporate branding standards and create trust by customizing your support experience, including chat
BeyondInsight Analytics
Centralized Management, Reporting, and Analytics
BeyondInsight is the industry’s most innovative, comprehensive privileged access management platform that maximizes visibility, simplifies deployment, automates tasks, improves security and reduces privilege-related risks. Gain a comprehensive view of the vulnerabilities that provide doors into an environment, as well as the privileges that present corridors to sensitive assets.
The security team benefits from being able to correlate vulnerability information with user activity, while IT gains a clearer view of how privilege policies impact overall security. This fusion of asset and user intelligence enables IT and Security to collectively reduce risk across complex environments.
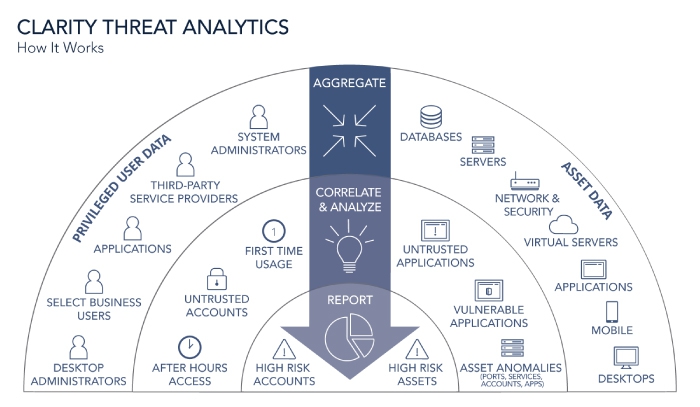
Combine User, Account, and Asset Threat Analytics for Unmatched Visibility
Analyze privileged password, user, and account activity, along with asset characteristics such as vulnerability count, vulnerability level, attacks detected, risk score, applications, services, software and ports. Included malware analysis capabilities help you correlate application, service, and process data with a continuously updated malware database. BeyondTrust connects the dots and flags the events you need to focus on, allowing you to act decisively and effectively prioritize risk mitigation.
- Aggregate user and asset data to baseline and track behavior
- Correlate asset, user and threat activity to reveal critical risks
- Identify potential malware threats buried in asset activity data
- Increase the ROI of your existing security solutions
- Generate reports to inform and align security decisions
BeyondInsight Analytics & Reporting
BeyondInsight contains a data warehouse solution with business intelligence and analytics. This module extracts data from the BeyondInsight database and then processes the data in Microsoft SQL Server Integration and Analysis Services. These cubes can be browsed in BeyondInsight, Microsoft SQL Server Management Studio, or using tools such as Microsoft Excel.
Using BeyondInsight, you can:
- Run reports on your vulnerability and attack data from the BeyondInsight management console.
- Subscribe to reports on a schedule for automatic delivery to a network file share or through email.
- Save report views to easily reuse a report with predefined parameters.
- Create report snapshots to save static views of report data.
- Interactively explore data and create and save custom reports with a Pivot Grid.
- Evaluate risk on assets using the Threat Analyzer.
- Find and examine audits using the Audit Viewer.



